Federal Policies for Life Sciences Research
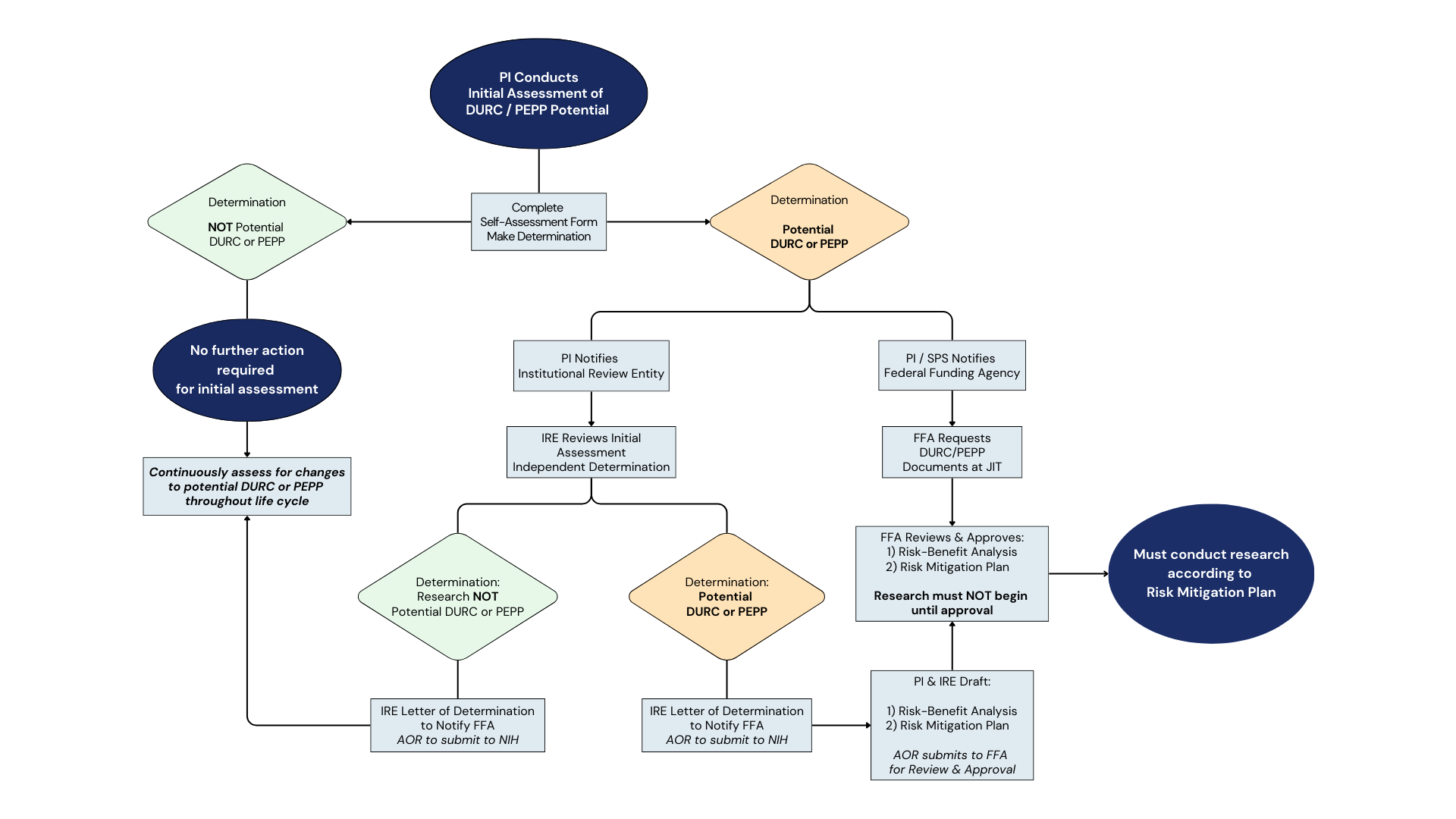
DUAL USE RESEARCH OF CONCERN (DURC)
Life sciences research is essential to the scientific advances that underpin improvements in public health and safety, agriculture (including crops and other plants and animals) the environment, materiel, and national security. Despite its value and benefits, certain types of research conducted for legitimate purposes can be utilized for both benevolent and harmful purposes. Such research is called “dual use research”. The current policy defines DURC as a subset of dual use research defined as life sciences research that, based on current understanding, can be reasonably anticipated to provide knowledge, information, products, or technologies that could be directly misapplied to pose a significant threat with broad potential consequences to public health and safety, agricultural crops and other plants, animals, the environment, materiel, or national security.
2012 Federal DURC Policy
2014 Institutional DURC Policy
POTENTIAL PANDEMIC PATHOGEN CARE AND OVERSIGHT (P3CO)
Research involving biological agents and toxins is essential to the scientific advances that improve national and global health and safety. Such research does not come without potential biosafety and biosecurity risks. Work with pathogens and toxins must be carefully considered. Appropriate risk mitigation strategies must be implemented to protect personnel and public health and safety.
Current regulations, policies, and guidelines regarding oversight for such work are as follows:
2017 OSTP Potential Pandemic Pathogen Care and Oversight (P3CO)
2017 HHS P3CO Framework
News from the NIH Office of Science Policy
MAY 7, 2025
Implementation Update: Improving the Safety and Security of Biological Research
Notice Number: NOT-OD-25-112
Key Dates
Release Date: May 7, 2025
Related Announcements
- January 10, 2025 – NIH Implementation of the U.S. Government Policy for Oversight of Dual Use Research of Concern (DURC) and Pathogens with Enhanced Pandemic Potential (PEPP). See Notice NOT-OD-25-061.
Issued by
NATIONAL INSTITUTES OF HEALTH (NIH)
Purpose
The purpose of this notice is to inform the biomedical research community of the following immediate actions NIH is taking in response to the May 5, 2025, Executive Order on Improving the Safety and Security of Biological Research.
- Policies, actions, and definitions defined in this Executive Order supersede NIH’s implementation of the White House Office of Science and Technology Policy (OSTP) May 2024 U.S. Government Policy for Oversight of Dual Use Research of Concern and Pathogens with Enhanced Pandemic Potential (DURC/PEPP Policy). Accordingly, NIH is rescinding NOT-OD-25-061.
- NIH will not accept competitive applications for grants and cooperative agreements submitted for due dates after today and/or R&D contract proposals submitted to solicitations issued after today for dangerous gain-of-function research, as defined in Section 8 of the Executive Order.
- NIH intends to suspend ongoing funding in accordance with guidance developed under Section 3(b) of the Executive Order. All NIH awardees should review ongoing research activities to proactively identify potential dangerous gain-of-function research and identify safe actions to halt such research and to effectively comply with guidance once established.
Background
NIH continues to emphasize that robust biosafety and biosecurity practices are essential for both promoting and protecting critical, life-saving research. As life sciences research evolves, so must the framework for safeguarding its conduct and results. The May 5, 2025, Executive Order on Improving the Safety and Security of Biological Research takes additional steps to strengthen oversight of research that could or will make a naturally occurring pathogen or toxin more dangerous to American citizens, and directs OSTP and the National Security Advisor to work with federal agencies to revise or replace existing policies overseeing this research. A new policy, to be delivered within 120 days, will replace the proposed DURC/PEPP Policy set to take effect May 6, 2025. Until this new policy is in place, research meeting the definition of dangerous gain-of-function research is to be paused.
For the purposes of this Notice and, as defined in the Executive Order, dangerous gain-of-function research means scientific research on an infectious agent or toxin with the potential to cause disease by enhancing its pathogenicity or increasing its transmissibility. Covered research activities are those that could result in significant societal consequences and that seek or achieve one or more of the following outcomes:
(a) enhancing the harmful consequences of the agent or toxin;
(b) disrupting beneficial immunological response or the effectiveness of an immunization against the agent or toxin;
(c) conferring to the agent or toxin resistance to clinically or agriculturally useful prophylactic or therapeutic interventions against that agent or toxin or facilitating their ability to evade detection methodologies;
(d) increasing the stability, transmissibility, or the ability to disseminate the agent or toxin;
(e) altering the host range or tropism of the agent or toxin;
(f) enhancing the susceptibility of a human host population to the agent or toxin; or
(g) generating or reconstituting an eradicated or extinct agent or toxin.
NIH will continue to provide updates regarding implementation of this Executive Order in alignment with the Administration’s guidance, including information on research halts or suspensions. Importantly, an effective and trustworthy oversight system is predicated on an interlocking framework with accountability shared across all partners. NIH encourages all life sciences researchers to assess their research portfolios to ensure we, as a research community, are proactively safeguarding the conduct of biomedical research to fulfill the NIH mission.
Inquiries
Please direct all inquiries to: NIH Office of Science Policy, SciencePolicy@od.nih.gov
MAY 6, 2025

On May 5, 2025, President Trump issued an Executive Order on Improving the Safety and Security of Biological Research, which pauses dangerous research that could or will make a naturally occurring pathogen or toxin more dangerous to American citizens, and directs the Director of the Office of Science and Technology Policy (OSTP) and the National Security Advisor to work with funding agencies to develop such a policy within 120 days. This new Policy is intended to replace the 2024 United States Government Policy for Oversight of Dual Use Research of Concern and Pathogens with Enhanced Pandemic Potential (DURC/PEPP Policy) and supersedes its implementation at NIH previously set to take effect today.
NIH will work closely with OSTP and our federal partners to ensure the safe and secure conduct of biological research. NIH will also provide more guidance regarding implementation of this Executive Order in the coming weeks.
Questions may be sent to SciencePolicy@od.nih.gov.
Link to Subscribe to OSP News
COMING SOON!
Updated UConn Policy on Life Sciences Research of Concern
Fact Sheet
Workflows
Templates